External Authentication Configuration
Overview of External Authentication
External Authentication can be enabled to centralize the management of user identities from an independent service provider on the hospital network. When configured, this provides additional security controls such as centralized password management and recovery, account lock-out, and time-of-day restrictions when the user logs in.
Centricity Perinatal Web supports two primary methods for authenticating a user’s credentials with an external authority: (1) SAML 2.0 token exchange with the site’s Identity Provider, and (2) LDAP to Windows® Active Directory.
For best workflow GE HealthCare recommends utilizing the SAML 2.0 token exchange as this can leverage the site’s existing single sign-on capability. The typical use of the Centricity Perinatal Web client will be from a mobile device outside the hospital network and will often require multi-factor authentication prior to launching Centricity Perinatal Web. By using the integrated SAML authentication the user would not be required to enter a username and password a second time when launching Centricity Perinatal Web.
How to Set Up External Authentication Through SAML 2.0
Requirements:
Users must have a Centricity Perinatal user ID that matches the external Identity Provider
Your site must have an Identity Provider that can provide a SAML 2.0 token to the Centricity Perinatal Web IIS service
You must have an IT person from your site who is already familiar with your Identity Provider configuration. This person must be prepared to work with GE HealthCare service to exchange key configuration information.
Once configured, your site’s IT will need to coordinate maintenance efforts to keep the configuration in sync when certificates are renewed or replaced on either the Identity Provider Server or the Centricity Perinatal Web Server
Planning:
As part of the implementation project, your GE HealthCare project manager and GE HealthCare Install Coordinator will identify requirements, resources and timing of the project to configure the interface from Centricity Perinatal Web (Service Provider) to your site’s Identity Provider solution.
Pre-requisites:
Your site’s Identity Provider Server needs to be installed and operational by your site’s IT and have a valid certificate. This certificate can be self-signed if that is consistent with your site’s policies.
The Centricity Perinatal Web Server, which is playing the role of Service Provider, needs to be installed and operational and have a valid certificate such as one from a certificate authority. Certificate requirements for the Centricity Perinatal Web server are described in the Customer Supplied Equipment Guide.
The single sign-on (SSO) test accounts that will be used in testing should be identified. The accounts can be real user accounts such as the system manager account; or be “test” accounts which then could be used by GE HealthCare service in the setup and initial testing. Please note, if using real user accounts, the individuals for those accounts will be responsible to do the testing. The accounts identified for testing need to be setup in the SSO system as well as in Centricity Perinatal Designer.
Configuration
This section outlines the high-level steps to perform the configuration of the interface between the Centricity Perinatal Web (CPN) Server and the site’s Identity Provider (IdP) Server.
(Step1) – Plan a meeting: It is recommended that the configuration for the interface be completed in a joint meeting between your site’s IdP configuration expert and the GE HealthCare service person assigned to the project. For optimum configuration and testing, this meeting should include screen sharing.
(Step2) – Site to configure IdP relying trust: Your IdP configuration expert will configure a new relying trust on your Identity Provider Server. In this configuration, the identifier to the CPN Web server can be “ConnectServices” or can be any naming convention that your site typically uses for service providers.
| Description | Example | |
|---|---|---|
| 1 |
Single sign-on service URL |
http://IdPServerAlias/idp/SSO.saml2 |
| 2 |
Single log-out service URL |
http://IdPServerAlias/idp/SLO.saml2 |
| 3 |
Identifier for the Identity Provider Server; depending on DNS configuration this may be a URL or Name |
http://IdPServerAlias/idp/services/trust |
| 4 |
Identifier for the CPN Web relying trust which the customer has configured on the Identity Provider Server. The customer IT can use any identifier here in the configuration; as long as GE HealthCare service configures the matching “string” in the SAML configuration |
ConnectServices |
| 5 |
A copy of the signing certificate from the IdP Server in .cer format, exported as 64-encoded. |
Signing_IdpServerAlias.cer |
| 6 |
Identification of which properties of the SAML configuration need to be true or false |
true or false |
| Description | Example | |
|---|---|---|
| 1 |
SAML Assertion Consumer Endpoint URL |
https://ConnectServerAlias/ConnectServices/saml/ Binding – HTTP-POST |
| 2 |
SAML Logout Endpoint URL |
https://ConnectServerAlias/ConnectServices/saml/ Binding – HTTP-Redirect |
| 3 |
A copy of the signing certificate from the CPN Web server in .cer format, exported as 64-encoded. |
ConnectServerAlias.cer |
(Step5) Your IdP configuration expert will import the CPN Web Server certificate and complete the relying trust configuration.
(Step6) GE HealthCare service will import the Signing IdP Server certificate
(Step 7) GE HealthCare service will edit the SAML configuration on the CPN Web Server given the guidance and information supplied by your site’s IdP configuration expert. The SAML configuration will appear similar to the following example.
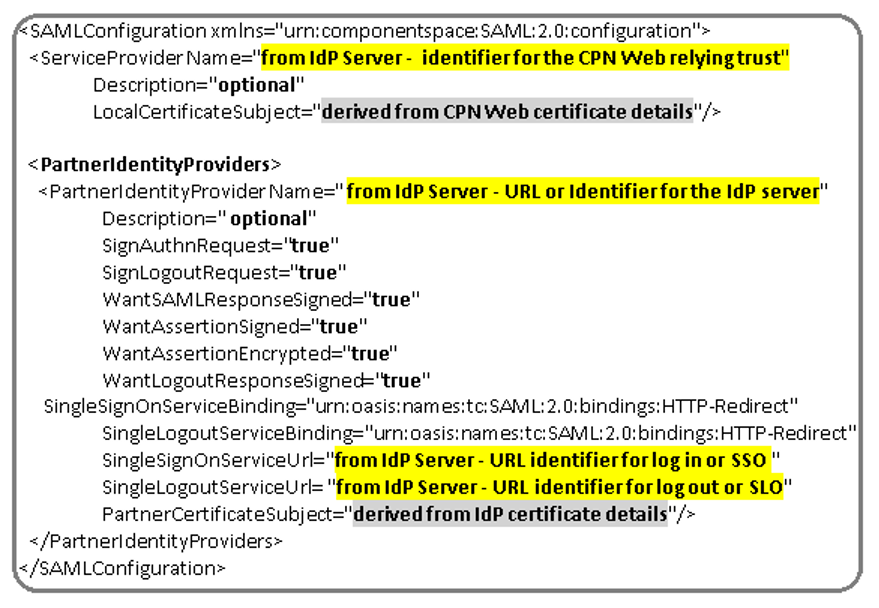
In the above example, the four fields in yellow highlight must match exactly to the IdP Server configuration and are supplied by your site’s IdP configuration expert. In addition, the fields currently shown with “true” need to be set to either “true” or “false” depending on what is enabled/configured on the customer’s IdP server.
(Step 8) Final review of configuration: Both GE HealthCare service and your site’s IdP configuration expert should review the configuration via shared screen an additional time to confirm it is setup properly confirming no typos, that the identifiers match exactly, and the true/false is set according to the site’s IdP Server configuration.
The user account in the set of tests can be from a real user such as the system manager or can be a test account. A test account has its advantages because GE HealthCare service can run tests with this account. A real user account will require the real user (such as the system manager) to perform the testing.
(Step10) Test with IdP Enabled. GE HealthCare service should enable the IdP interface. The browser, if currently opened should be re-opened and navigate to the CPN Web URL. Navigate to the CPN Web URL on a browser. At this point, if the interface is working you will be redirected to the site’s single sign-on page and you will not see the CPN Web Log in page. The user will then enter the same user ID and password as done on the previous step. After entering in the credentials, the CPN Web application should display. Confirm the user can select a patient and view a fetal monitoring strip with no errors.
(Step11) Additional testing can be performed using different browsers, devices (such as phones or personal laptops), and the testing can include exercising log in, log out, auto log out, etc to confirm behavior of the interface is working as expected.
(Step12) Maintenance. Your site is responsible for managing certificates on your IdP Server as well as the CPN Web Server. These certificates should be renewed before they expire. Please contact GE HealthCare service for a planned service event to update the configuration on this interface should you either renew or replace the certificate on your IdP server or the CPN web server.
Troubleshooting
How To Set Up External Authentication Through LDAP
Information on how to set up External Authentication through LDAP can be found in the System Configuration Reference Manual for Centricity Perinatal.